‘Tis the season of resolutions – and as we charter our course for 2020, it’s also a time for reflection as business leaders for organisations large and small ask themselves, what can we learn from the year before? Where did we triumph, and where did we fall?
There’s one thing that’s sure to unite the entire community. Consulting firm Juniper Research estimated that cybercrime cost businesses over US$2 trillion in 2019. And as we add new potential vulnerabilities to the network – for example, IoT, connected devices and edge computing – the amount of damage cybercrime inflicts and the number of attacks is only set to increase.
However, with the average cost of disruption from a cyberattack already costing SMBs USD1.9 million (Ponemon Institute), the reality is that breaches hit smaller businesses that much harder than their larger counterparts.
Entering the New Year, the question therefore is – where are the threats coming from? And how do you avoid falling victim? Here’s our take on the top 3 most common hacks according to the Cisco SMB Cybercurity Report, and how to identify when you’ve been targeted:
#1) Ransomware
Ransomware – malware that is distributed through means such as email phishing, malicious advertising and exploit kits – is a long-time favourite of the enterprising cybercriminal. It encrypts a target’s data and requests for a ransom in exchange for releasing the files – which, incidentally, isn’t guaranteed. Typically, the attacker demands payment in a form of cryptocurrency such as bitcoin, to keep transactions anonymous and difficult to trace.
SMBs are the perfect target for this kind of attack – not only do they typically not have the resources in place to prevent the breach, they are also more inclined to pay the ransom in order to avoid downtime and disruption to their operations.
How do you know to look out for said ransomware? The answer to that is simply vigilance. Most times, ransomware is unleashed because someone’s run an application or downloaded a file from an unverified source. So check every email that comes in or link/homepage you land on – is it from someone in your organisation? Is there an official signature? Is the domain name the same as that used by your firm? Be extra careful when opening a file or attending to an uncanny request – did your colleague really put in that request or send you that file? It also pays to ensure that you regularly patch and back up your files.
#2) Advanced Persistent Threats
An advanced persistent threat (APT) is a clandestine cyberattack on a computer network where the attacker gains unauthorized access to the targeted network and remains undetected for an extended period. Until the APT is discovered and rectified, the hacker will monitor, intercept, and relay information and sensitive data.
Typically speaking, an APT’s main goal is to eyeball or steal data – such as valuable intellectual property – rather than cause a network outage, denial of service or outright infection. Again, an SMB can be an attractive target for an APT – particularly if they form part of the supply chain that links up with a large MNC. In that same vein, a bootstrapped startup that deals in cutting edge machine learning and artificial intelligence algorithms is also at risk – if their IP is lost or worse, copied, that could spell the end of their operations.
APTs are not the easiest to detect. For one, the hackers aren’t necessarily ‘active’ – they just sit there. And the means to plant an APT may not be ‘visible’ to the naked eye. Very often, hackers use social engineering – the art of trawling social media to gain valuable information – to gain the access they need. The would-be attacker may impersonate details of an employee, send an email with a file that does nothing – but that’s all it takes for an APT to be launched.
As such, SMB employees should pay heed to what they share about their organisation on their social media platforms, and not discuss sensitive matters over unencrypted channels. Having a solution that analyses your web traffic for any unusual behaviour also helps – our Cisco Umbrella can spot anything that isn’t supposed to be there.
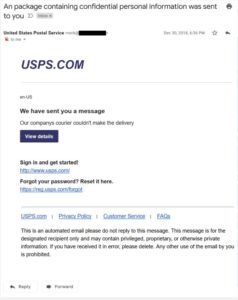
#3) Phishing
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source – they’ve progressed a fair bit from the ‘Nigerian prince’ scams of yesteryear. However, the principals remain the same – if successful, the victim is coaxed into providing confidential information. Usually, the end goal of phishing is for financial gain, but it can also serve a more sinister purpose, such as setting the stage for serious attacks.
Typically, the ‘phishers’ will impersonate companies that the target does business with, such as banks or financial services, or the cloud-based apps and software they use to run their own organisation, such as Dropbox and Office 365. There’s also the classic fake invoice, sent by someone impersonating the finance department and requesting payments of some sort.
Again, email is the #1 culprit. SMB employees should be double wary – especially if the email comes from the finance department requesting for payment upfront, or from your business leader directly requesting for sensitive information. Checking the email for spelling errors, or incorrect/foreign domains will help to identify if it’s a phishing attempt or not.
It’s not always easy to spot the fake from the authentic, but a bit of education can go a long way to ensuring a robust cyber defense. Not sure where your organisation stands? Check out the Cisco SMB security checklist now to assess your business.