Security breaches continue to make headlines, affecting organizations of all sizes and industries. Understanding how breaches unfold and how to stop adversaries before the ‘Boom!’ is critical. Leveraging a proper architecture is vital to reducing risk and protecting sensitive data. This blog shares key prevention strategies focusing on hardened infrastructure, visibility, network segmentation, detection and response, and Cisco’s integrated security portfolio designed to secure your environment, ‘Left of Boom!’
The Breach Timeline: The Starting Point
Breaches rarely happen instantaneously. They unfold over time, as attackers infiltrate, gain footholds, move laterally through networks, and escalate their privileges for further misuse.
“When we speak of ‘Boom!’, we refer to a cyber incident or breach event, be it an individual device compromise, credential theft, access to a secured system, or an incident causing an outage.”
After initial device compromise, attackers may exploit weak segmentation and lack of visibility to expand their scope for reconnaissance, embed into additional systems, or get closer to the ‘crown jewels’ of the environment. This embedding, a calculated and stealthy expansion is more prevalent if they are state-sponsored actors with a target asset, such as highly confidential information.
From the Office to Anywhere
Today, work is no longer confined to a specific location like the office. Employees work from home, coffee shops, airports, and across hybrid environments, expecting seamless access to corporate resources as if they were physically on site.
“Work is a function, not a location.”
In addition, most employees have used their corporate devices for personal activities, increasing exposure to threats. For example, opening personal Gmail can deliver uninspected emails containing malicious links, attachments, or embedded data. Relying solely on endpoint security is risky because it often detects
threats only after they’ve reached the device and may be based on what we know already – static signatures and fingerprints. Modern threats are stealthy, leveraging legitimate system files and evading detection. Even more concerning – what if there is little or no visibility into that asset’s state back to our operations center?
The Layered Defense Model – Policy Decision Points
Endpoint protection is essential but should not be the sole security focus. As we’ve seen, no endpoint solution is a guarantee of protection. Instead, a comprehensive, layered approach should include:
- Endpoint Protection and Detection: Continuous monitoring and analysis of endpoint activity to detect and respond to threats quickly, including malware, fileless attacks, and suspicious behaviors.
- Email Protection – Content and Security Filters: Scanning emails for data loss, malicious attachments, phishing links, and harmful content before they reach users to prevent initial compromise.
- Secure Internet Access and Private Application Access: Protecting user web traffic with reputation checks and AI-based threat detection to block access to dangerous sites and downloads. Secure connectivity to private applications is also necessary to avoid potential eavesdropping while making it a seamless experience for the user.
- Logging and Integration with Security Operations: Collecting detailed logs and telemetry from endpoints, email, and network access – and forwarding them to Security Operations Centers (SOCs) for real-time threat detection, correlation, and response.
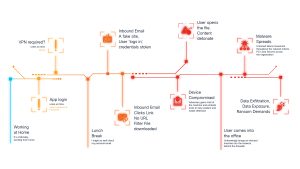
Entering the Office, Perimeter Protection Bypassed
An unknowingly infected device belonging to a user or a malicious insider could connect to the corporate network, bypasses perimeter defenses. We typically grant a higher level of trust because of the physical location of an asset inside the environment. Without strict internal controls, this device can spread malware laterally, moving unchecked across the environment, opening file shares, and accessing sensitive resources. This lateral movement can happen without detection by traditional inline security devices because we cannot force every packet or flow through these devices, especially at the access networks. We saw this with Lockbit, Wannacry, and many other rapidly spreading worms.
“Attackers often use legitimate tools and credentials to blend their activities with normal network traffic and evade alerts.”
 Without continuous monitoring and strong segmentation, malware can silently propagate, increasing the breach’s impact and making containment far more difficult.
Without continuous monitoring and strong segmentation, malware can silently propagate, increasing the breach’s impact and making containment far more difficult.
‘Left of Boom!’
Left of Boom is a simple way to talk about everything that needs to happen before a big cyber incident. It would be akin to what you do to protect your house before a big storm happens, like boarding up windows, packing emergency kits, and knowing evacuation routes. In cyber terms, it’s:
- Inventory – Knowing all the devices and users on your network and making sure only the right ones are allowed in, including IOT devices.
- Proper authentication of employees, guests, and contractors.
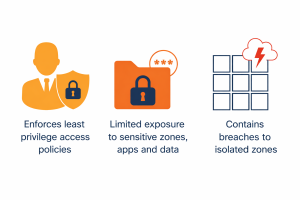
- Segmenting your network based on Inventory and Authentication, reducing the scope of a blast.
- The placement of gateway controls, like SD-WAN and Firewalls, ensures that access control policy is enforced.
- When our sensing devices such as Firewall, IPS or NDR signal an event, trigger a workflow to isolate the affected system and mitigate risk to the rest of the environment.
- Left of Boom is all about being proactive, not reactive, reducing the scope before scrambling to prevent a full-on breach. The biggest component here is a Secure Infrastructure.
Secure Infrastructure: The Foundation of Trust
Segmentation and detection rely on a secure, trusted infrastructure based on:
- Hardware Trust: Trust to validate the integrity of firmware and boot up.
- Software Trust: Verifying startup trust and software integrity
- Configuration and Compliance: Role-based access controls, Day 0 onboarding, and operations.
- Centralized Policy Management: Unified control for consistent policy enforcement.
- Embedded Telemetry and Analytics: Continuous monitoring that enables proactive threat detection and supports Zero Trust response options.
Focus Left of Boom
“Stopping widespread breaches requires the assumption that devices will be compromised and breaches will happen.”
Taking proper measures to enhance user authentication, network segmentation, endpoint and email security, and maintaining a secure infrastructure foundation will help to better protect an organization. Cisco’s unified security approach simplifies this comprehensive defense, helping organizations reduce risk and respond quickly if, and when, attacks occur.
#SecuredAI #AIDefense #NetworkSecurity #CiscoAI #CiscoSecurity