The manufacturing industry has been resistant to change in the past – but the pandemic forced them to re-think their operations and revisit digitization plans that enabled significant automations. Neglecting to do so wasn’t an option as lockdowns and safety regulations made it impossible to carry on with traditional processes.
Today, business leaders in the manufacturing industry are focused on boosting overall equipment efficiency (OEE), business continuity and more recently, resilience. This is the future-forward end state that these organizations want to achieve to gain visibility across their operations, secure themselves in the face of growing cyber threats as they digitize, and enable staff and workers to be in a safe working environment and spend their time efficiently. It’s what will ultimately allow these organizations to get an edge over their competitors.
Manufacturers are pinning their hopes on technologies such as the internet of things (IoT), private 5G networks, and Wi-Fi 6, which can help transform traditional facilities into smart factories . Unfortunately, things aren’t as simple as they seem.
When bringing a factory online to make it ‘smart’, there are many technologies that are leveraged, including artificial intelligence (AI), sensors, cloud computing, and big data analytics. Together, they make interesting use cases come alive, directly impacting OEE and maximizing output (quantitatively and qualitatively).
An automotive factory, for example, leveraged a combination of the aforementioned technologies and high-definition cameras, to speed up inspections. More than a 1,000 images were taken of each finished chassis, transmitted via the cloud to an AI-powered software, that allowed the organization to identify defects – even those that were invisible to the naked eye. Doing so not only helped automate the task but also uplifted product quality to deliver better results.
Building a smart factory involves connecting Programmable Logic Controllers (PLC), Robots, AGV’s and other industrial assets to one or more wireless industrial networks, as well as the organization’s supervision network (SCADA, DCS, and other ICS, for example) to the group WAN to bring everything online. This process creates a larger attack surface area from a cybersecurity perspective and means that IT teams must incorporate these new vulnerabilities into their security agenda, effectively bringing operations technology (OT) into the fold.
While most IT professionals are familiar with what needs to be done to extend the boundaries of their security deployment, execution is a challenge for two reasons: first, not all tools in use can support an expanded scope of work merging IT and OT; second, talent is in short supply which means organizations need to acquire automation capabilities to cover a larger surface area.
If you’re struggling to visualize the problem at hand, think of a factory you can relate to and imagine attaching sensors to the equipment inside it. The sensors are intended to collect data from the machine, connect to the internet via the organization’s private 5G network or WiFi-6 routers, and send it to the organization’s cloud-based manufacturing software to leverage cloud-based analytics to boost OEE, raise operational efficiencies, and improve manufacturing output.
The ERP can crunch the data to create actionable insights, allowing the management to make all sorts of decisions about its operational facilities, supply chains, and more. However, since the machines are now connected to the internet, they’re also vulnerable to cyberattacks. Getting hacked now not only puts data and financials at risk but could also halt operations inside the factory.
Becoming ‘smart’ is something companies cannot avoid if they want to remain competitive. The smart thing to do while they’re going down the smart-path is to leverage a robust solution that integrates IT, cloud, and industrial control networks (ICS) to expand the boundaries of security to cover IT as well as OT. Of course, this is one of Cisco’s specialties – it’s what one of our portfolio solutions, Cyber Vision, does very well.
OT Security: Same as IT security?
For some leaders, their organization’s failure to leverage its experience with IT security to seamlessly protect the OT environment that has now come online is difficult to picture.
The fundamental difference they need to note is this. The life of IT systems is about 3 to 5 years. For OT systems, the lifespan often expands up to 30 years. When IT security solutions are brought into the OT environment, they lack this context and can’t account for the many physical and operational attributes of these machines.
IT teams are also often guilty of making organization-wide security decisions without input from OT engineers. As a result, deployments aren’t as effective as they should be. To ensure that security measures are implemented successfully, IT and OT teams must work in harmony through each phase of the cybersecurity process.
At the start of the IoT revolution, the media was rife with headlines about bad actors hacking smart thermometers, smart fish tanks, and more – to gain access to the organization’s network and systems. Today, this gives a unique insight to IT teams looking to secure their smart factories: they need to secure against internal as well as external threats.
Since ‘connected’ machines are integrated with the rest of the organization’s systems, someone with physical access to them could upload a virus, ransomware, or trojan horse (or other kinds of malware). IT teams need to see contractors such as repair technicians and maintenance crew as well as disgruntled workers leaving the service of the manufacturer as possible bad actors and secure the equipment accordingly.
This is the kind of niche insight that OT engineers can bring to the table when IT teams are thinking about expanding their organization’s security boundaries.
Truth be told, in the new normal, organizations cannot afford to be siloed. They need collaboration, between IT and OT, and the rest of the organization, in order to be successful.
While we’ve emphasized the value of security directly, the reality is that adapting to the changes in the manufacturing industry hinge on another key factor: the experience offered to stakeholders. Fortunately, experience is determined by the degree of flexibility of security capabilities which makes adopting and enabling cutting-edge applications and workflows possible. As a result, a focus on security in manufacturing becomes even more critical.
The upside in taking a converged approach to IT and OT security
Cisco’s customers value the fact that Cyber Vision gives them not only visibility of the OT assets but also provides alerts about any abnormal behavior by performing deep packet inspection of OT traffic. It also offers a great degree of automation capabilities with the ability to interface with other Security Information and Event Management systems. However, the real value of converged IT and OT security lies in breaking down the departmental barriers between the silos and finding common ground to secure the organization in a way that makes defense manageable, intelligent, and (dare we say) easy.
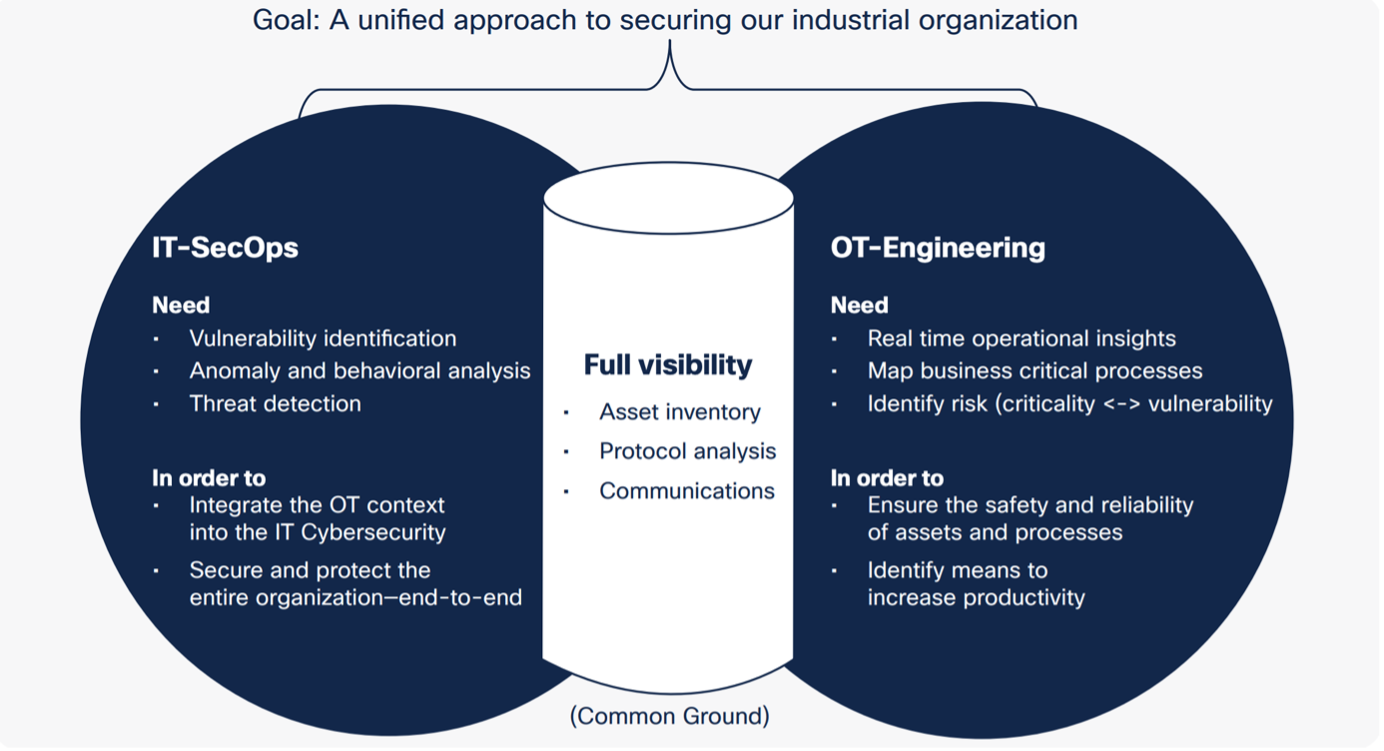
Cisco’s customers buy into the idea that IT and OT teams need to work together and collaborate as the boundary of the organization’s security deployment expands in line with its increasing surface area and exposure.
Instead of building new and disjointed OT security methodologies, organizations that want to keep their smart facilities secure need to leverage existing tools and investments to better secure OT environments without disrupting production.
Ultimately, securing the industrial enterprise means extending the existing IT security tools (with existing skills, knowledge, and budget) into OT and bringing the OT information (devices, process, events, etc.) and OT engineer’s knowledge into IT. If you’re keen to learn more about Cyber Vision or understand how our team can help protect your factory as you bring it to life, check out our resources page now.