
Over the past two decades, organizations have invested significant resources and time to strengthen their security posture and defend against the growing myriad of threats. However, many leaders are starting to assess whether their organization’s security strategy is sustainable. This is being driven in large part by one key factor – complexity.
The fact is that cybersecurity has become complex for most organizations. However, the reality is that it doesn’t have to be. To solve this, we need to first understand the factors that are driving the current complexity for organizations.
Firstly, over the years most organizations have deployed cybersecurity tools or solutions to address the specific issues or risks at the time. As organizations have grown, and their issues evolved alongside, it has led to an increase in the number of technologies/tools across their infrastructure. The complexity comes from the fact that these tools don’t always integrate, and if they do it may not be uniform across provisioning, automation, monitoring and alerting. To put it simply – this creates complexity.
Second, with workloads transitioning to the cloud, and users becoming more and more mobile, organizations are left with the hefty task of maintaining security on all fronts, which becomes more and more challenging. This constant quest for better/more tools inherently increases complexity and is not sustainable.
Third, an organization’s infrastructure tools usually get deployed based on needs. Some of these needs are permanent, but many could be temporary, or seasonally required. In most cases, these ad-hoc solutions add to environment complexity leading to threats that are harder to identify and fight. The rapidly changing threat landscape also requires IT security teams to constantly update and review their workflows. Over time leaders can’t help but notice the extra levels of complexities and inefficiencies that this drives.
In addition to these factors, Cybersecurity threats are constantly changing and evolving. From malwares, denial of service attacks, application vulnerabilities, the list is long, and keeps growing.
Finally, the number of tools needed to secure your environment, the skillset required to design and manage these tools (and the integration), means that teams struggle with their workloads and find it even harder to recruit talent with the requisite experience.
Addressing complexity: The SASE way
Cisco has championed Secure Access Service Edge (SASE) since inception.
Cisco’s SASE help your organization address
- Make your business more agile by leveraging the cloud for immediate scalability
- Gain more simplicity, predictability, and intelligence by removing infrastructure complexity
- Enjoy instant global coverage, with the ability to provision thousands of locations in minutes and scale up and down your level of service, features that you use, and the number of connections in your subscription
- Adopt zero trust network access including user identity and device health, on a per-session basis
- Best in class visibility to quickly pinpoint application and network performance issues
- Converge networking and security in the cloud with end-to-end observability
- Connect and secure access to applications, data, and the internet for anywhere users
- Optimize performance by leveraging fastest, most reliable, and secure path to the cloud
SASE is more than an architecture; it’s a significant step forward in all-round network and security for organizations of all sizes. SASE is a network architecture that combines software-defined WAN capabilities and cloud-native network security.
By the numbers…

Converging your security solutions
At Cisco we are proud of the intelligent security solutions we have built and maintained over the years. Our customers appreciate more about our portfolio that the number of tools and solutions we have work together, seamlessly. This provides the ultimate converged line of defense, true to the definition of SASE. Something most other vendors may struggle with. Working with multiple vendors, however, poses challenges to achieving an efficient and converged SASE state.
SASE is most effective when hardware and software control points are well integrated into a single dashboard, allowing organizations to accelerate response times, automate their defense, and elevate their security posture while offering a great experience to users across the board.
We believe Cisco SASE vision presents as your business partner in digitizing your business simply and safely. Our architecture combines single pane of glass network and security, intelligent and converged line of defense, solutions that are natively integrated, and best of all a single vendor.
If you’re looking to explore how SASE can help you and learn more about how Meraki, Umbrella, and Duo can upgrade your security posture quickly, check out this resource we created with Gartner to help you.
SASE Breakdown – For you engineering teams
A popular Cisco SASE architecture would combine Cisco Meraki cloud managed networking, Umbrella and Duo.
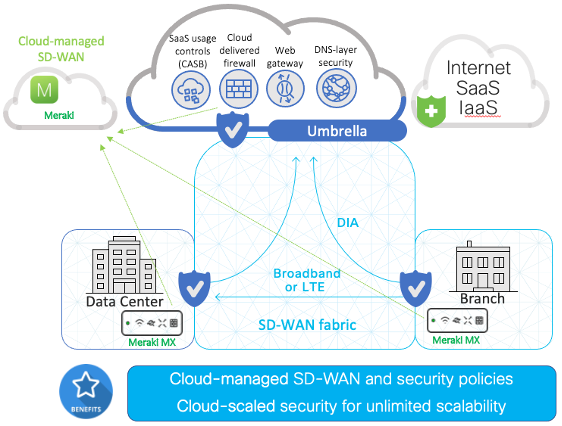
The first product provides cloud-managed secure connectivity, the second complements it with cloud-first security, and the third glues the two together to manage digital employee identification. This trio protect devices, applications, and networks against all threats.
Let’s imagine what this means for a mid-sized organization with 3,000 employees spread across 18 offices in 12 countries in North America, Europe, and APJC.
Employees would first be prompted by Duo for authentication, irrespective of their location, what device or network they use, and also irrespective of which application they are accessing.
Corporate traffic to applications in the cloud (or their data centers), and user traffic to the internet are equally protected by Umbrella. Networks are provisioned, managed and at all times monitored by Meraki.
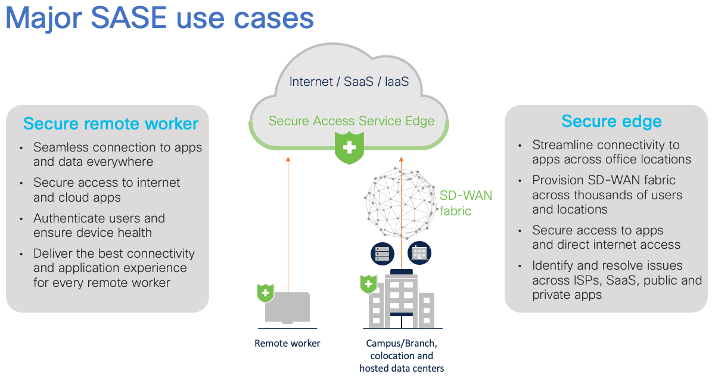
In a remote working scenario, leveraging this trio means that employees can connect directly to applications with a single middle layer to protect, encrypt, and secure their connection. For those that returning to office, there’s a whole host of other benefits – especially if the organization has deployed connected cameras and sensors to keep staff safe and its facilities in optimal shape.
In every organisation there’s bound to be new employees and employees resigning on a regular basis. The trio work together to make it easy for the organization to deploy policies that automate much of the IT-security related tasks around such events.
Finally, beyond security, organizations are more and more focusing not just on employee experience, but consistency and reliability of their resources use.
A SASE deployment can provide great visibility into the network to ensure everything is running as smoothly and seamlessly as possible.