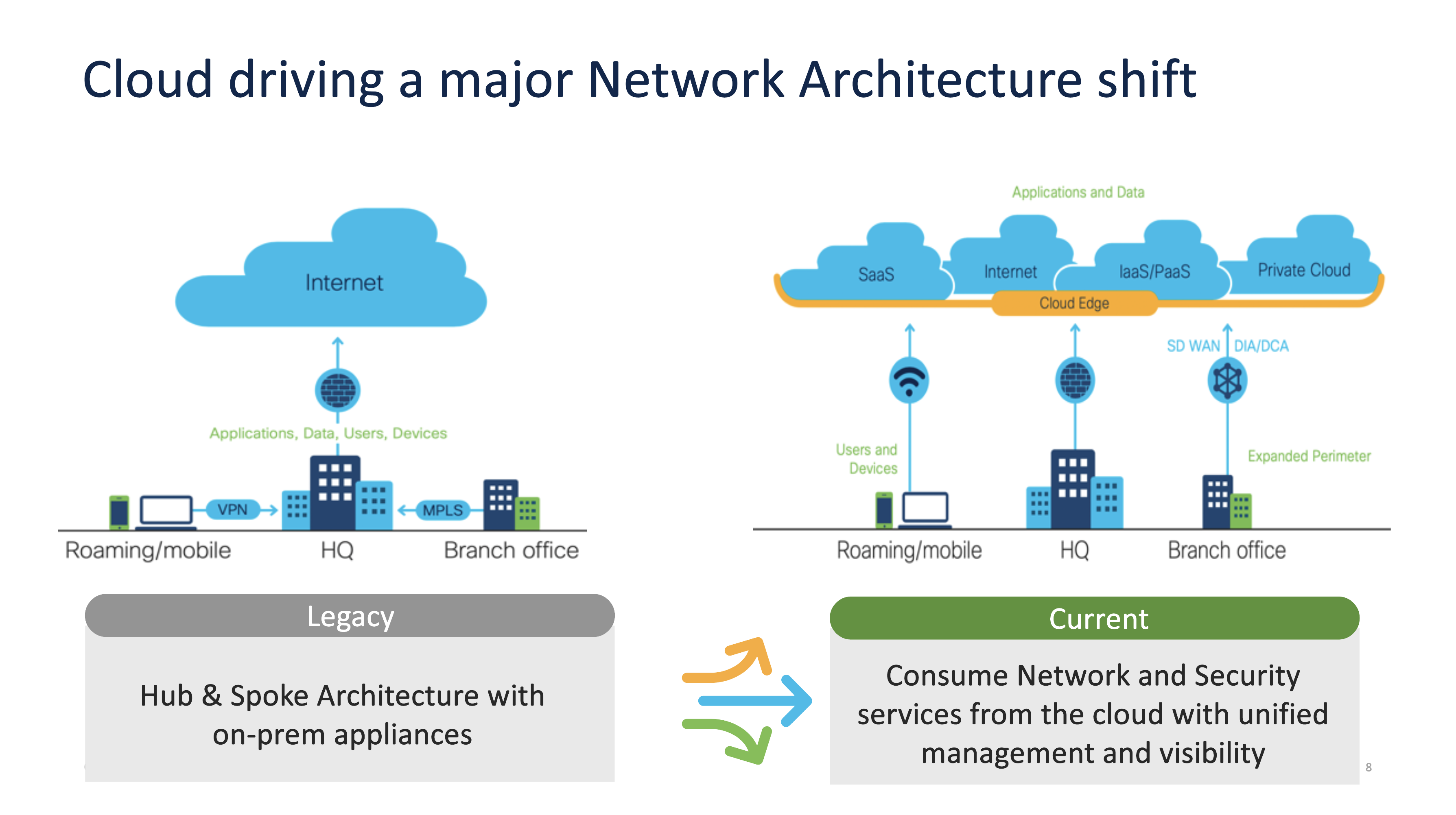
The cloud is driving an inherent architectural shift in the way networking and security services are being consumed by our customers. In today’s hybrid environment, with remote work being the norm and customers demanding application-based services, cloud services are critical. This is driving CIOs and CISOs to work more closely than ever before, to not just deliver seamless experiences but also keep the organization’s infrastructure secure.
Truth be told, leaders across organizations have understood that the cloud is not a destination, it’s a journey to an operating model that needs to be constantly scaled, upgraded, and optimized. In this cloud-accelerated environment, the biggest challenge, the fundamental problem, is cybersecurity. Securing an organization’s cloud-based architecture in an ever intensifying threat landscape is difficult, especially when the different parts of the security solution are disjointed and don’t speak with each other. This is where SASE can help.
In a previous blogpost, I explained Gartner’s construct of SASE as a network architecture that combines software-defined WAN capabilities and cloud-native network security services including zero-trust network access, secure web gateways, cloud access security brokers, and FWaaS (firewalls as a service) – which is delivered as a cloud-based service.
An observation I made was that organizations with a relatively mature digital infrastructure can leverage SASE right out of the box and use its automation capabilities to further enhance their threat intelligence and defense mechanisms. Given how quickly the concept of SASE is evolving, I believe it is the most cutting-edge security option out there today.
SASE is proof that security is moving to the cloud. However, there’s something important we must take note of: We’ve highlighted that SASE is made up of several components such as SD-WAN which drive connectivity and FWaaS and CASB which provide control – but what really drives differentiation and delivers efficiencies is how each of them converge.
It’s the state in which threat detection and mean time to respond are minimized and protection against bad actors is maximized. In this state, policy roll-outs are seamless, orchestration is truly agile, and the organization has complete observability across the network. Once SASE’s fundamental components converge, cloud operations converge to provide synergies that help the organization double down on efficiencies while creating a truly world-class layer of defence around every inch of its infrastructure across planes.
Unfortunately, the different parts of a SASE deployment don’t always work together to provide a single dashboard in a unified ecosystem.
Before we go further, let’s put things into perspective. If you provide your employees with the flexibility to work from a café, their homes, or the office, allow them to use any network, and need them to access critical applications via devices that might not necessarily be issued by the company (and hence, not entirely trusted), you can immediately start to image the security threats your network and architecture might face.
To this, add the complexity of applications that support partners, customers, and a wider ecosystem and you begin to see how the various components of SASE we discussed previously help with easy management, automation, and quick detection and response to threats.
When SASE’s building blocks work in isolation, they don’t offer the full protection intended by the model. To really shine, SASE’s various components must work like Lego blocks to really guard the organization irrespective of who needs to access which application from where.
At Cisco, we feel confident talking about SASE because we offer all of the components involved, which makes like simple for developers who can focus on the implementation rather than looking into integration complexities. Our customers combine our best-in-class networking, connectivity, security, and observability capabilities into a single subscription service: delivering seamless, secure access to any application, anywhere users work.
Individual components that make up SASE such as software-defined WAN capabilities and cloud-native network security services including zero-trust network access, secure web gateways, cloud access security brokers, and FWaaS (firewalls as a service) can all succeed piecemeal – but making them all work together is where organizations really set themselves apart from the rest.
According to Gartner, organizations are increasingly looking to invest in these components. By 2023, to deliver flexible, cost-effective scalable bandwidth, 30% of enterprise locations will have only internet WAN connectivity, compared with approximately 15% in 2020. By 2024, 30% of enterprises will adopt cloud-delivered SWG, CASB, ZTNA and branch office firewall as a service (FWaaS) capabilities from the same vendor, up from less than 5% in 2020. By 2025, at least 60% of enterprises will have explicit strategies and timelines for SASE adoption encompassing user, branch and edge access, up from 10% in 2020.
Since Cisco’s solutions come from the same portfolio, they all work together, making convergence simple and effective – and truly unlocking value in SASE investments overall. A converged SASE deployment is where policy, visibility, and operations are streamlined, and automations become possible.
Your SASE investments win when all its components converge
Every organization is different. They not only have different needs but also have different legacies. Further, their vision for the future in terms of cloud-based applications, digital experience, and technology transformation are all different. Hence, every organization’s journey to SASE is truly unique.
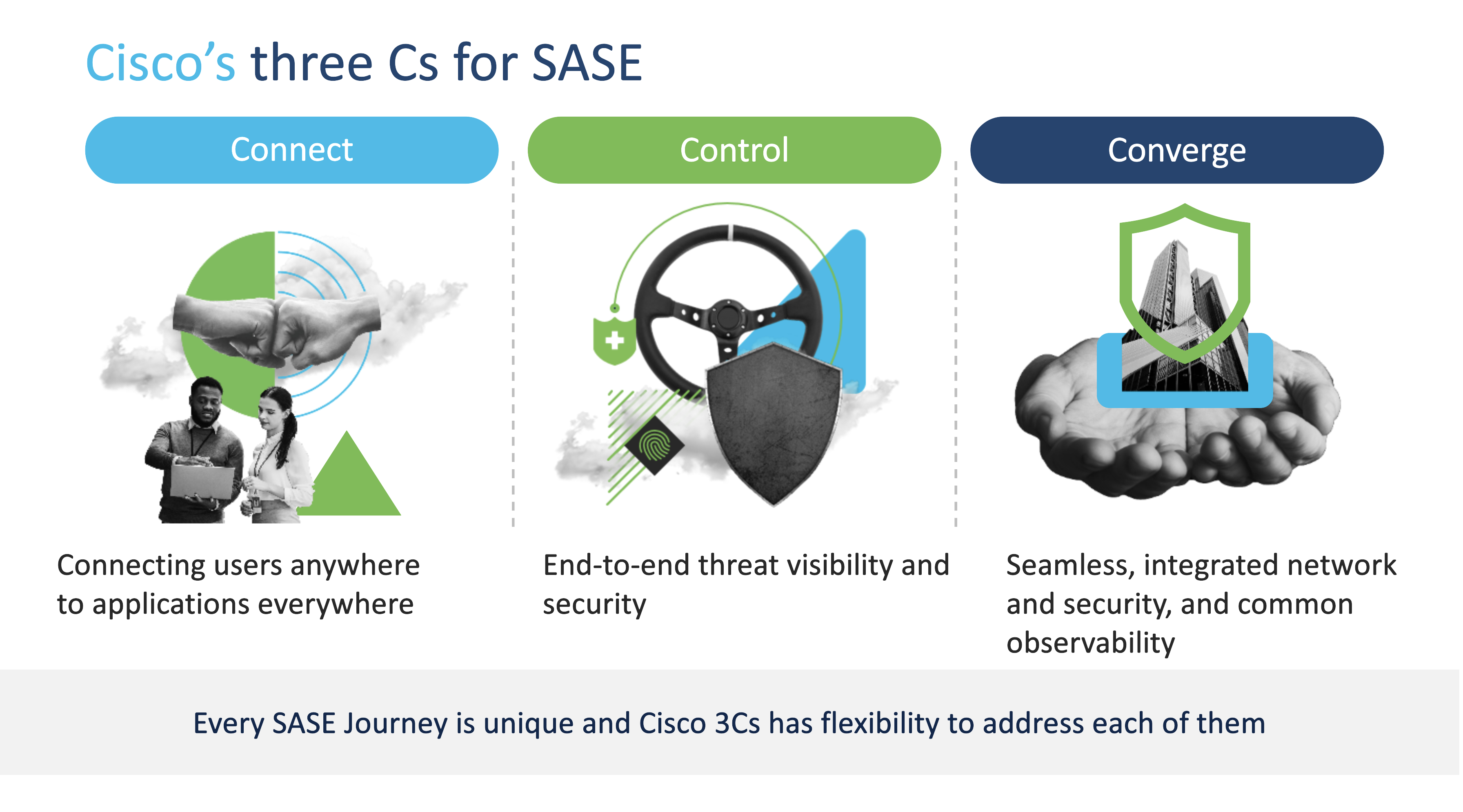
Leaders who want to truly get the most out of their SASE investments need to see their deployment in a simplified manner. Cisco’s 3C model, for example, suggests that each SASE journey be broken up into three parts – one that looks into how the organization ‘connects’ its applications and users, the other that evaluates how the IT team ‘controls’ the threat landscape, and the last one which helps ‘converge’ network and security.

The ‘connect’ segment is usually the easiest to take care of. In most cases, it involves migrating to SD-WAN with direct internet access and cloud onramp. To ‘control’ the ecosystem and environment better, leveraging virtual private network (VPN) and multi-factor authentication (MFA) is the recommended way forward. Finally, ‘converge’ implies the use of unified management and visibility across SD-WAN and security.
From personal experience, as soon as we split things up into these three segments, customers tend to find that they’re already on their own journey to SASE. Working with our team then helps them identify their choices, create a plan, and start gaining some momentum with regards to deploying SASE. Ultimately, the reality is that making progress is important because security is critical in today’s cloud-first era. We all need to take action, and we need to do it now.
To best chart your roadmap to SASE convergence, here’s some advice from Gartner.
I already read this article ang i learned that the all organization is different
Security is the omportant thing if using cloud