The Australian Government recently announced an increase in the malicious cyber activity against Australian networks and the current targeting of organisations by a sophisticated cyber actor, raising the alarm for many businesses across the country. Further to this, the Federal Government will make the nation’s largest ever investment in cyber security, with $1.35 billion to boost cybersecurity capabilities over the next decade. This has acutely increased the awareness and alert to the threat of cyberattacks, and a good reminder to us all that cybersecurity is a shared responsibility across government, business, and individuals.
These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes. Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative. The challenge we have is how to help organisations reduce the time it takes to detect if they’ve been compromised, and if they’ve been owned.
We now know the large-scale cyberattack was the Copy-Paste Compromises campaign, and the Australian Cyber Security Centre (ACSC) Advisory 2020-008 provides insight and advice into the attack networks. The adversary is determined to have used a mixture of techniques for initial access.
What was the impact? Firstly, they exploited known vulnerabilities in public-facing applications. When this didn’t work, a phishing approach was used, with malicious links and/or attachments to emails, in an attempt to harvest legitimate access credentials or deliver malware to the recipient. Legitimate credentials were accessed, harvested using phishing, credential dumping, and the location of credentials in stored files. Once the attackers obtained these credentials, they moved laterally and established persistence using remote access services.
In a landscape that is continuously changing, understanding attacks and learning from them is key to improving cybersecurity posture. Here’s what we recommend.
Actions to increase your Cyber Posture – Detect and Remediate
The most effective way to confront the dynamic threat landscape is to make security pervasive. This is even more important as we continue to work from home and remotely – wherever employees are, and your data resides.
Deploy Multi-Factor Authentication (MFA) from Duo Security
One of the top recommendations from the ACSC advisory is to enable multi-factor authentication across all remote access services. We know that MFA should cover remote access services, external-facing services, and critical internal services and servers. Doing so mitigates the risk of unauthorised access due to stolen credentials, persistence, and lateral movement throughout the environment.
Duo provides MFA that is easy to use for employees and easy to manage for IT professionals. Duo’s solution integrates simply with hundreds of different resources in an IT environment, and the flexibility in choice of authentication method makes it as intuitive as possible for employees to verify their identity. Protection for the workforce through MFA is the first phase in Cisco’s advice on establishing a Zero Trust architecture, followed by micro-segmentation for the workload and network access control for the workplace.
Find out more:
- Duo and Australia’s Essential 8 Cybersecurity Strategies
- How Duo Maps to Australian Cyber Security Center Remote Worker Guidelines
Protect your internet facing devices and applications with Cisco Umbrella
In addition to multifactor authentication, it’s important to have a holistic approach to cybersecurity, such as a first line of defence with DNS-layer security.
DNS-layer security detects requests for, and prevents establishment of, outbound connections to malicious and potentially malicious domains and/or IP addresses; these connections can provide identification of infected hosts in your environment.
Backed by threat intelligence from Cisco Talos security researchers, Umbrella also identifies potentially malicious domains based on inference from historical data, association with known malicious domains or IP spaces, or use of techniques like Domain Generation Algorithms or typo-squatting. Secure Internet Gateway (SIG) capabilities extend the DNS-layer capabilities to include full URL analysis and content inspection with integrated Advanced Malware Protection (AMP) and previously unseen file analysis with Threat Grid.
From small businesses without dedicated security professionals to multinational enterprises with complex environments, it is simple and fast to gain a new layer of breach protection and internet-wide visibility on and off your network.
Further reading:
Cisco’s platform-approach covers these two essential pieces of advice and extends to map to a full defence-in-depth strategy.
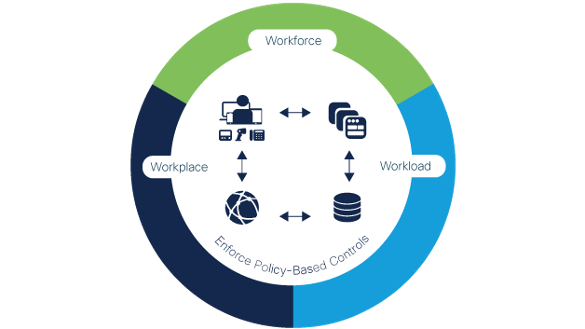
Secure access for your workforce, workloads, and workplace
Cisco Zero Trust Security, is a comprehensive approach to securing all access across your networks, applications, and environment. This approach helps secure access from users, end-user devices, APIs, IoT, microservices, containers, and more. It protects your workforce, workloads, and workplace.
Cisco SecureX was recently announced at Cisco Live, and is a platform that covers network, endpoint, cloud and application and enables a Zero Trust approach by tying together continuous threat detection and continuous threat verification. It is crucial that organisations have the capability to quickly determine if they are 1) Exposed, or 2) being owned.
The ever-changing threat landscape, speed to response is critical and that’s where SecureX threat response can help. Threat response accelerates threat hunting and incident management by aggregating and correlating intelligence and data across your infrastructure in one view. Threat response is a key feature of SecureX. There’s more to come on the visibility, automation and efficiency delivered through SecureX. As well, keeping on top of all the changes in the threat landscape is important, as cybersecurity is constantly evolving, changing and challenged.
Join us to learn more on July 8 and July 14 at 2:00pm AEST when we will host Cisco Secure Insights Summit with some inspiring speakers on zero trust, security strategy and the importance of teamwork in cybersecurity industry. Click here to learn more and to register.
CONNECT WITH CISCO
LET US HELP
Call us: 1.800.553.6387 - Ext 118
US/Can | 5am-5pm Pacific Other Countries