The NIS2 Directive is a Directive introduced by the European Commission and is a natural progression and enlargement of the preceding EU cybersecurity Directive, NIS 2016 NIS 1 Directive.
It represents an essential piece of legislation within the European Union aimed at bolstering the security and resilience of critical infrastructure and essential services. NIS2 seeks to address the evolving cyber threat landscape and expand its scope to cover a broader range of sectors, and make Europe a safer place to live and work.
NIS2 is a directive, and as such, each member state of EU must
formulate its own laws, interpreting them based on the directive.
With its impending implementation, organizations must act now to ensure compliance, protect their operations, and maintain a robust cybersecurity posture. It’s important to note that NIS2 holds management bodies accountable for implementing and overseeing their organization’s compliance (Article 20 , Governance), possibly leading to fines and temporary bans on managerial roles, including at the senior level.
Understanding the NIS2 Directive
NIS2 establishes two categories for entities within its scope: “essential” and “important.” Both categories must adhere to the same requirements, but the differentiation lies in the supervisory measures and penalties. Essential entities must comply with supervisory requirements upon the introduction of NIS2, while important entities will face ex-post supervision, which means that action is taken if authorities receive evidence of non-compliance.
It introduces new provisions, such as incident response and crisis management, supply chain security, and enhanced supervisory measures. NIS2 expands the scope to include critical sectors like public administration, waste management, and space, further emphasizing the need for comprehensive security measures.
Key Reasons to Act Now
Enhanced Regulatory Requirements: With more rigorous cybersecurity and reporting obligations, organizations must act now to avoid potential fines and penalties. Implementing the necessary security controls and processes will not only ensure compliance but also contribute to a stronger security posture. By 17 October 2024, EU Member States shall adopt and publish the measures necessary to comply with this Directive. They shall apply those measures from 18 October 2024.
Evolving Cyber Threat Landscape: Cyber threats are becoming more sophisticated, and the potential for devastating attacks on critical infrastructure is increasing. Early preparation and proactive measures are essential for minimizing the impact of cyber incidents on operations and reputation.
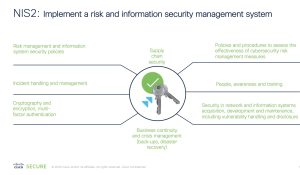
The measures referred to within (Article 21) of the documentation shall be based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents and shall include at least the following security requirements as noted in Figure below: NIS2 implement a risk and information security management system.
Steps for NIS2 Readiness: How Cisco Secure can Help
Let’s evaluate how well Cisco’s offerings align with the directive’s focus area.
Risk analysis and information system security policies
This section aims to conduct a thorough risk assessment to identify and prioritize vulnerabilities, threats, and potential impacts on critical assets and operations.
Cisco Vulnerability Management reduces risk efficiently with data-driven vulnerability prioritization.
In addition, Cisco’s service offerings, such as the Secure Architecture Framework, Threat Modeling exercise, and CISO workshops, provide the necessary methodologies to guide actions aimed at enhancing security posture and reducing risks.
Incident handling (prevention, detection, and response to incidents)
NIS2 introduces a revised incident reporting timeline. Both essential and important entities are required to promptly notify any incident with significant impact. Within 24 hours, they should issue an early warning and share initial assessments of the incident’s nature with the relevant competent authority or CSIRT. Following this, a comprehensive notification report, including an incident assessment, severity, impact, and indicators of compromise, must be submitted within 72 hours. Lastly, a final report is to be communicated within one month.
From a technological standpoint, the extensive capabilities of the Security Suites delivered by Cisco Security Cloud powered by rich set of offers , can provide the necessary telemetry and analytics, along with detection and response solutions, enabling Cisco to play a supportive role in achieving NIS2 compliance.
In addition of the products portfolio, Cisco Talos Incident Response provides customers with rapid cybersecurity incident response capabilities to assist with the investigation of cybersecurity breaches. We also provide services proactively to help prepare for an incident.
Business continuity and crisis management
This term, as stated in the official documentation, refers to address backup management, disaster recovery, and crisis management.
In the event of a cybersecurity incident or crisis, Cisco offers Talos incident response services to help organizations mitigate the impact and recover effectively. In Particular, Cisco Talos Incident Response (CTIR) provides a full suite of proactive and emergency services to help you prepare, respond and recover from a breach. CTIR enables 24 hour emergency response capabilities and direct access to Cisco Talos, the world’s largest threat intelligence and research group.
Training and Education: Cisco offers training programs and certifications in cybersecurity. These programs help organizations develop the skills and knowledge needed to effectively manage and respond to cybersecurity threats and crises.
Supply Chain Security: Assesses your supply chain’s security posture and implement measures to mitigate risks, ensuring that suppliers and partners adhere to the same security standards as your organization.
Cisco recognizes the important role of supply chain security in a comprehensive Cisco cybersecurity strategy. Under that strategy, we deploy a capability that continually assesses, monitors, and improves the security of the Cisco supply chain throughout the entire lifecycle of our solutions. Our commitment is to strive to meet our customers’ integrity expectations.
Our solutions are genuine (not counterfeit).
Our solutions operate as our customers direct them to work
(not secretly controlled by or transmitting data to unknown parties)
Aligned with supply chain security, the Software Bill of Materials (SBOM) provides an important layer of transparency and accountability to help customers keep their network healthy and software supply chain secure. The SBOM Request Form allows Cisco customers with a Cisco.com account to receive SBOMs for Cisco software products. Cisco believes that SBOMs are a foundational element necessary to provide greater security and trust in all technology and then better secure the supply chain. The Cisco Panoptica solution generates a software bill of materials (SBOM) for each image, identifies the vulnerabilities associated with each layer, analyzes deployment templates for configuration risk, and ensures best practice conformity via CIS (Center for Internet Security) Benchmarks.
Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure. The Cisco Cybersecurity portfolio provides substantial value and visibility across various domains, including endpoint security, network security, cloud security, and application security. It equips Security Operations with the latest innovations, such as AI-powered XDR (Extended Detection and Response), to detect and respond to incidents in an orchestrated manner.
In summary, Cisco’s cybersecurity portfolio provides organizations with comprehensive security measures, acquisition of signals across endpoints, networks, clouds, and applications, safeguarding against a wide range of threats and enhancing overall security posture.
The use of cryptography and encryption: Cisco is recognized as a leader in the field of cryptography, leveraging its expertise to provide secure communication and data protection solutions. With a strong focus on innovation and research, Cisco has developed advanced cryptographic algorithms ( including support of Quantum resistant ) and protocols that meet the highest industry standards. Our leadership in cryptography is evident through their commitment to securing network communications, protecting sensitive information, and enabling secure connections across various platforms. Cisco’s robust cryptographic demonstrate our dedication to ensuring the confidentiality, integrity, and authenticity of data, making them a trusted leader in the field.
Conclusion
The NIS2 Directive is a crucial step toward securing Europe’s critical infrastructure and essential services in an increasingly interconnected world. Organizations must act now to prepare for the new requirements, safeguard their operations, and maintain a robust cybersecurity posture. By proactively addressing the challenges and necessities posed by the NIS2 Directive with the Cisco Secure portfolio, organizations can not only ensure compliance but also strengthen their resilience against the ever-evolving cyber threat landscape.